Harnessing Real-Time Situational Awareness in Physical Security Planning
Most physical security plans are built using static information such as site layouts, historical incidents, known vulnerabilities, and expected conditions. That information is necessary, but it is not complete. Security environments do not remain static, and plans built solely on fixed assumptions tend to lose effectiveness as conditions change.
Real time situational awareness helps close that gap. It allows planning and advance work to reflect what is actually happening, not just what was expected to happen.
This post examines how real time data supports physical security planning, advance assessments, and ongoing risk and vulnerability work, and why it should be treated as a core input rather than a supplemental one.
What Situational Awareness Looks Like in Physical Security
In physical security, situational awareness means understanding what is happening across people, places, and conditions, and recognizing when those conditions begin to shift. It includes what is occurring on site as well as what is developing around it.
This can include:
How many people are present and how they are moving
Where access points are functioning as intended and where congestion is forming
Current weather and environmental conditions
Ongoing incidents or medical responses
Shifts in threat posture or regional activity
Situational awareness does not come from a single system or location. It is built through the combination of real time data, clear communication, and trained observation by personnel in the field.
Planning With Data That Can Change
Advance work and security planning often rely on assumptions made days or weeks before operations begin. While necessary, those assumptions can become outdated quickly.
Real time data allows planners to:
Reconfirm or adjust risk assumptions
Identify emerging vulnerabilities
Modify staffing, access control, or monitoring priorities
Align plans with current conditions instead of forecasts
When planning incorporates live data, it becomes more resilient. The plan is no longer a fixed product. It becomes a framework that can adapt as conditions evolve.
Advance Assessments as Living Documents
Advance assessments are often treated as one time deliverables. Once completed, they are rarely revisited unless a significant issue occurs.
In practice, advance assessments should function as living documents. Real time situational awareness supports this by:
Providing continuous feedback on environmental conditions
Highlighting gaps between expected and actual operations
Allowing threat evaluations to be refined during execution
This approach reduces the disconnect between planning and operations, which is where many security failures occur.
Situational Awareness in Ongoing Risk and Vulnerability Assessments
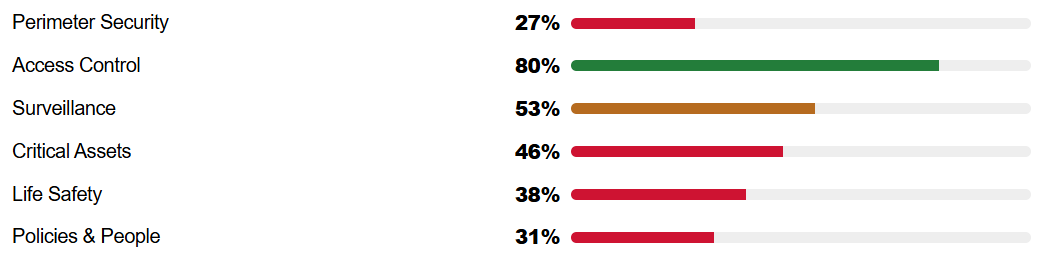
Risk and vulnerability assessments are typically conducted on a set cycle, but the conditions they evaluate change far more frequently. Situational awareness helps bridge that gap by providing context that static assessments cannot capture on their own.
For those who regularly conduct assessments, real time awareness supports the process by:
Revealing how vulnerabilities shift under normal versus peak conditions
Identifying access points or controls that perform differently in practice than on paper
Exposing temporary risks created by staffing changes, construction, weather, or special activity
Showing how congestion or environmental factors affect response time and capability
Highlighting emerging threats that were not present during the last assessment cycle
Rather than treating assessments as snapshots in time, situational awareness allows them to function as evolving evaluations. Observations made during operations can be fed back into risk scoring, assumptions can be revisited, and mitigation strategies can be adjusted.
For assessors, this approach improves accuracy. Risks are no longer based solely on design intent or historical data, but on how systems and people actually perform under real conditions. Over time, this leads to more defensible assessments and more realistic mitigation planning.
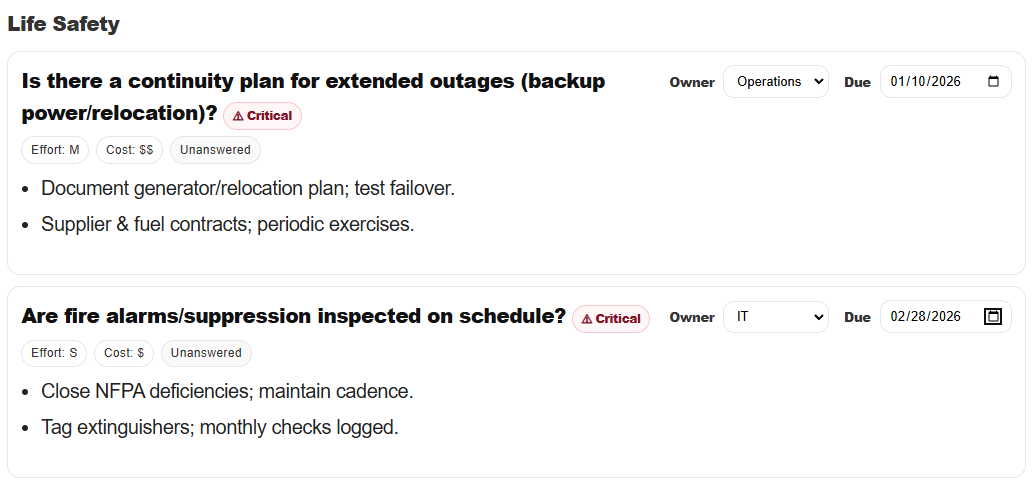
Identified Gaps
Risk and vulnerability assessments are most effective when identified deficiencies are actively tracked rather than simply documented. Assigning ownership ensures that each issue has a responsible party, while clearly defined due dates establish expectations for corrective action and future review.
This approach supports continuity between assessment cycles, helps prevent repeat findings, and provides a clearer picture of risk posture over time. By treating deficiencies as actionable items with accountability and follow up, assessments become part of an ongoing risk management process rather than a one time exercise.
The Limits of Technology
Technology enables situational awareness, but it does not create it on its own. Sensors, cameras, dashboards, and alerts are only useful when supported by clear processes and trained personnel.
Effective use of real time data requires:
Defined decision authority
Clear information flow
Personnel trained to interpret data, not just observe it
Regular review of what information actually informs decisions
Without this structure, real time data can overwhelm rather than clarify.
Closing Thoughts
Physical security planning cannot rely solely on what was known yesterday. Conditions change, risks evolve, and assumptions expire.
Real time situational awareness allows planners and operators to see those changes as they occur and adjust accordingly. When integrated into advance work and ongoing operations, it strengthens security not by predicting every outcome, but by improving understanding in the moment decisions matter.
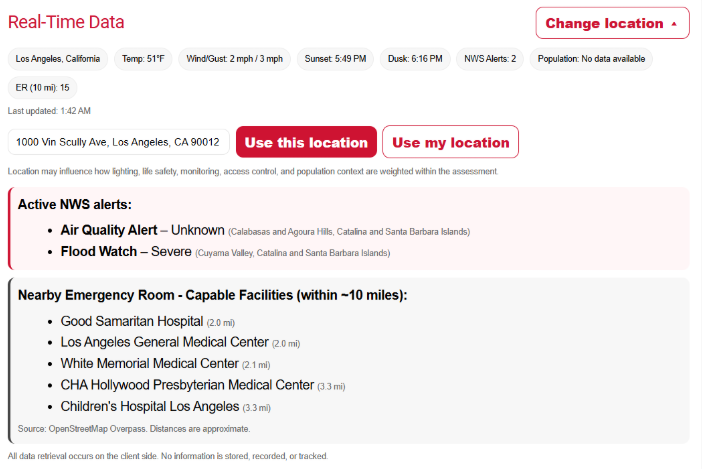
Red Slice Group maintains a free security assessment tool available at https://www.redslicegroup.com/free-assessment. The assessment is designed to support planning, advance work, and general situational awareness by providing structured questions and real time contextual inputs. The tool operates entirely on the client side. All data queries occur locally within the user’s browser and no data is stored, recorded, tracked, or transmitted by or to Red Slice Group. The assessment is intentionally under continuous improvement as conditions, risks, and best practices evolve. Feedback from practitioners and users is welcome and helps inform future updates. The tool is intended as a practical resource to support security thinking and discussion. It is not a replacement for formal risk or vulnerability assessments, professional education or training, operational judgment, site specific verification, or independent fact checking of locations, conditions, or capabilities.
-
Isaiah La Masters is a public safety and emergency management professional with extensive experience in physical security, critical infrastructure protection, and large-scale emergency preparedness. He is the Founder and Principal Consultant of Red Slice Group, LLC, and has served in multiple roles supporting emergency coordination, training, and exercise at the state and local levels. Isaiah holds an Associate of Arts in Liberal Arts and Political Science, a Bachelor of Science in Homeland Security and Emergency Management, and is currently pursuing a Master of Science in Public Safety—Homeland Security at Liberty University. Passionate about leadership and organizational resilience, he is committed to strengthening collaboration between agencies, responders, and communities to build a safer, more resilient world.